Overview
The Multi-Factor Authentication (MFA) module in EstateFlow ERP provides an added layer of security to protect sensitive company and project data. MFA requires users to verify their identity through more than one method — typically a password plus a time-sensitive authentication code. This is especially important in real estate development environments where ERP systems manage financial data, vendor contracts, and confidential project documentation.
By implementing MFA, you reduce the risk of unauthorized system access, even if a user’s password is compromised.
[Insert Screenshot: MFA Settings Dashboard]
Key Features & Benefits
-
Enhanced Security – Protects against password theft and brute-force attacks.
-
Multiple Authentication Methods – Supports SMS, Email OTP, and App-based authentication (e.g., Google Authenticator).
-
Configurable Enforcement – Apply MFA to all users or selected user groups.
-
Device Recognition – Option to trust recognized devices for faster login.
-
Integration with Access Roles – MFA can be linked to specific role permissions.
-
Real-Time Alerts – Notify admins of failed MFA attempts.
Pre-Requisites & Access Rights
-
Ensure the MFA Module is enabled under Admin > Module Settings.
-
Assign access rights in Admin > Roles & Permissions for:
-
Enabling/Disabling MFA
-
Viewing MFA Logs
-
-
Confirm that user profiles have up-to-date email addresses and/or phone numbers for verification codes.
-
For app-based authentication, ensure the device has a compatible authenticator app installed.
[Insert Screenshot: MFA Role Permissions Setup]
Step-by-Step Instructions
Enabling MFA for All Users
-
Navigate to Admin > Security Settings > MFA Configuration.
-
Toggle Enable MFA to On.
-
Select the Default Authentication Method (SMS, Email OTP, or App-based).
-
Choose whether MFA applies to All Users or Selected Roles.
-
Click Save Settings.
[Insert Screenshot: Enable MFA Settings Page]
Enabling MFA for Specific Users
-
Navigate to Admin > Users.
-
Select the User Profile.
-
Under the Security Settings section, toggle Enable MFA.
-
Select the preferred MFA method for that user.
-
Click Save.
[Insert Screenshot: User Profile MFA Setup]
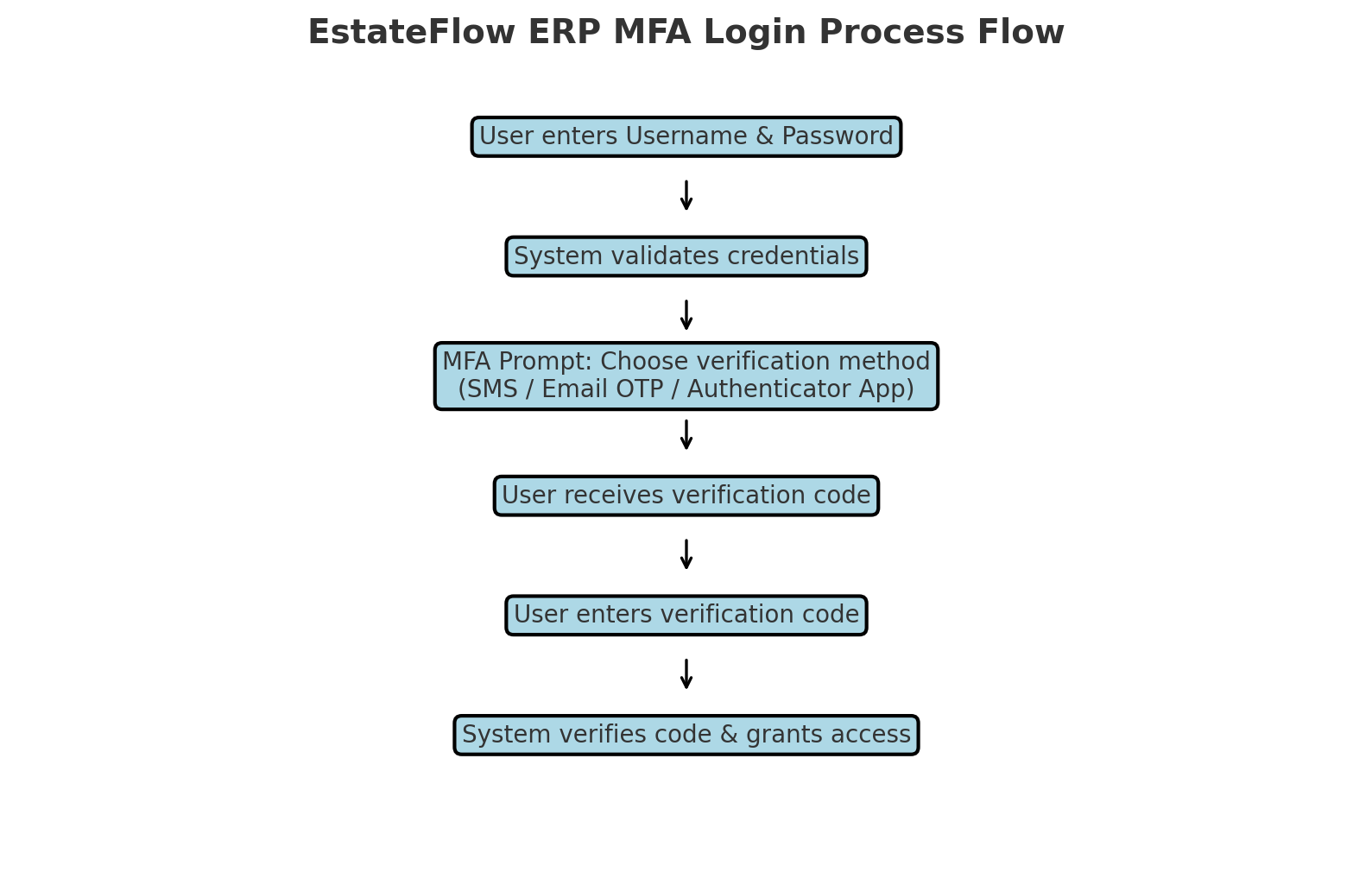
Logging in with MFA Enabled
-
Enter your username and password as usual.
-
The system will prompt for an MFA Verification Code based on the configured method:
-
SMS – Code sent to registered phone.
-
Email OTP – Code sent to registered email.
-
App-Based – Code generated by authenticator app.
-
-
Enter the code and click Verify.
-
If Trusted Device is enabled, you can skip MFA on that device for a defined period.
[Insert Screenshot: MFA Login Prompt Screen]
Tips & Best Practices
Tip: Use app-based authentication for higher security compared to SMS or email OTP.
Best Practice: Require MFA for all users with Admin or Financial roles.
Tip: Regularly audit MFA logs to detect unusual login attempts.
Best Practice: Encourage users to enable MFA on all integrated apps connected to EstateFlow ERP.
Troubleshooting & Common Issues
Issue: User not receiving OTP.
Solution: Verify that the user’s registered email/phone is correct and accessible.
Issue: Authenticator app not syncing.
Solution: Ensure device time is correctly synced; rescan the QR code if needed.
Issue: MFA prompt appears unexpectedly.
Solution: Check Trusted Device settings; clearing browser cache or switching devices will trigger MFA again.
[Insert Screenshot: MFA Error Message Example]
Glossary & Notes
-
MFA (Multi-Factor Authentication): A security process that requires more than one verification method.
-
OTP (One-Time Password): A time-sensitive, single-use password for authentication.
-
Trusted Device: A user device recognized by the system to bypass MFA for a set period.
Note: MFA settings should align with your organization’s IT security policy.
Caution: Disabling MFA for privileged accounts may expose sensitive data to security breaches.